Key Takeaways
If the past few years taught us anything about cybersecurity, it’s that hackers aren’t slackers. (Feel free to quote that zinger!) Instead, they execute sophisticated, multi-tiered attacks targeting all-sized businesses across various industries. As a result, many of us have transformed into cybersecurity experts. Or, at least, we’d like to think we are!
Let’s put your knowledge to the test and see how you measure up. Take the 10-question quiz below for an extra shot of fun and then continue reading the post.
1. What type of device is targeted by malware more, Android or macOS?
You’re right if you guessed that cybercriminals routinely target Android devices more than Apple. Be proud, Steve Jobs. Roughly 98% of mobile malware targets Android devices. However, macOS malware has skyrocketed by 165% during the past year — but the stats don’t stop there.
- Email delivers 92% of all malware.
- 51.45% of malware consists of Trojans.
- Ransomware made up 7 out of every 10 malware payloads.
- At any given moment each week, malware infects more than 18 million websites.
- When malware hit businesses this year, it took 34% of them a week or more to get back access to their data.
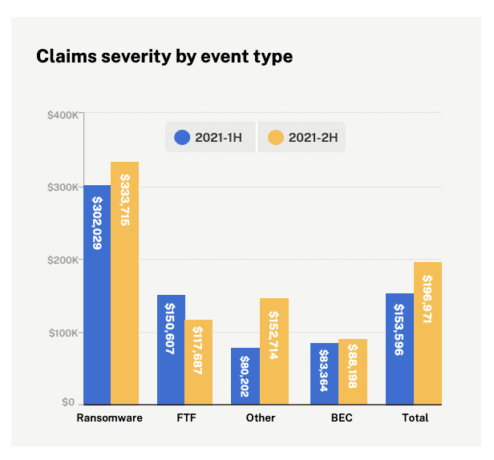
2. How much is the average ransom demand?
We’ll consider “a boatload” as the correct answer one day. However, today the average ransom demand has recently jumped by 20% to $1.8 million.
- Commercial insurance claims reflected a 20% increase in ransom demands during the last half of 2021.
- Businesses spend more than $75 billion each year dealing with ransomware costs.
- Over 40% of insurers had clients experience a minimum of six ransomware attacks.
- The cost of the Equifax breach was more than $4 billion.
Source: Coalition
3. What percentage of companies infected with ransomware run current endpoint protection?
Get ready to say ouch because roughly 75% of companies infected with ransomware were running updated endpoint protection. As mentioned earlier, cybercriminals have become far more sophisticated than before. No longer do these hackers launch haphazard campaigns. Instead, they rely on stealthy and fine-tuned methods.
- More than 50% of information security professionals don’t think their company is ready to ward off a ransomware attack.
- Downtime due to ransomware costs companies around $8,500 per hour.
- Nearly 90% of current IT professionals work with clients that have experienced ransomware attacks in the past year.
- Every 11 seconds, a new business falls victim to ransomware.
- Cybercriminals create roughly 1.5 million new phishing sites each month.
Cyber Risk Management Guide
4. What percentage of ransomware victims end up paying the ransom?
This number might bring tears to your eyes — and we’re sorry. Still, around 40% of ransomware victims end up paying the ransom. Cybercriminals genuinely define the term “bully.” Here are some more cringe-worthy stats you need to know.
- Nearly 25% of the c-suite is willing to pay at least $20,000 and up to $50,000 to regain access to their encrypted data.
- Of all the organizations who pay the ransom, only 30% ever see all of those dollars again.
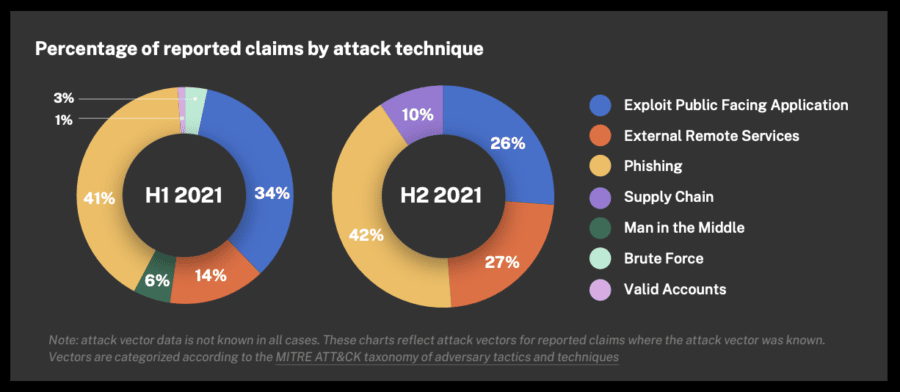
- Navigating the realm of social engineering proves to be a hackers’ favorite, as revealed by 60% of IT professionals who identify new employees as the foremost cyber risk for companies. Explore effective methods of dealing with risk in this dynamic landscape.
- Roughly 98% of cyber attacks depend on social engineering.
- The top security threat for 56% of IT decision-makers remains targeted phishing attacks.
5. CEO fraud is now a $_____ billion scam.
The magic number is $12 billion beans. CEO fraud is a spear-phishing email attack where hackers spoof company email accounts and impersonate a CEO, attempting to gain access to sensitive information and ultimately cash. Companies encourage employees to report malicious emails, but it rarely happens.
- Around half of all phishing sites now use HTTPS.
- Only 3% of victims report infected emails to management.
- Phishing plays a role in 21% of ransomware attacks.
- Malicious email attachments deliver 66% of malware installations.
- A malware attack costs companies an average of $2.4 million per attack.
6. What’s the number one disguise for distributing malware?
We already partially answered in the previous list; however, the precise answer is that fake invoices take the cake as the number one disguise for malware. It’s uncomfortable to think that fake invoices trick more professionals than any other disguise. And for the sake of your entertainment, malware gets worse.
- Malware costs companies an average time of 50 days.
- Lost information is the most expensive component of a cyberattack, accounting for 43% of costs.
- Roughly 65% of companies have more than 500 employees who are never prompted to change their passwords.
Source: Coalition
7. What causes nearly 50% of data breaches for small businesses?
The answer is a jagged pill to swallow. Here’s why. Negligent employees or contractors are the root cause of 48% of all data breaches for small businesses — ouch! We think employees are assets, but sometimes they can be liabilities. It’s worthwhile to provide employees with the tools to stay cyber safe.
- Third-party mistakes account for 41% of data breaches for small businesses.
- Funds Transfer Fraud (FTF) losses grew by 69%.
- Social engineering plays a role in nearly 33% of all data breaches.
- Out of all data breaches, 43% involved small businesses.
- Roughly 41% of companies have more than 1,000 unprotected sensitive files (i.e., credit card numbers, health records).
8. What’s the average cost per lost record?
A buck and a half is how much each lost record costs on average. Even though the average cost per lost record is $150, many files aren’t protected. Here are some more alarming statistics.
- Experts predict that cybercriminals will steal 33 billion records next year.
- Roughly 21% of all files aren’t protected whatsoever.
- By the end of this year, nearly 65% of the global Gross Domestic Product (GDP) will rely on a digital system.
- Crypto mining plays a role in 90% of remote code execution attacks.
9. If you notice an incorrect payment, how soon must you report it to increase the likelihood of recovering the funds?
Despite ransomware being in all the headlines during the past few years, FTF cases continue to rise. If you notice an incorrect payment, you must report the loss within 48-72 hours of the transfer. Otherwise, your likelihood of recovering those funds decreases significantly or disappears altogether.
- FTF losses totaled more than $220 million last year.
- The sum of all fraud losses in 2020 reached $3.3 billion.
- Wire transfer fraud increased by 13% YoY for real estate-related transactions.
- Only 29% of businesses involved in FTF cases ever recover their entire funds.
- Wire fraud scams targeted ⅓ of all wire transfers.
10. Insurance plans solved what percentage of reported incidents for policyholders cost-free?
Insurance plans solved 46% of all reported incidents to policyholders at no cost. What lessons can we learn from these statistics?
For starters, ransomware is a ruthless and destructive force, but it’s not the only strategy cybercriminals use. So, keep your ears and eyes open to the threats potentially targeting your industry. Also, training your employees goes a long way — a lot further than most companies want to admit. Arm new hires and current employees with the tools they need. Lastly, protecting your assets with insurance plans is far more cost-effective than cleaning up the aftermath.
Pro Tip ↓
Is your company protected? For a free Cyber Risk Assessment, click here: Cyber Risk Assessment.
Understanding the details of what coverage your company needs can be confusing. Founder Shield specializes in knowing the risks your industry faces to make sure you have adequate protection. Feel free to reach out to us, and we’ll walk you through the process of finding the right policy for you.
Insurance Rebuilt, End-to-End