Key Takeaways
As cybersecurity becomes a frequently talked about topic, businesses everywhere are concerned. What does a typical business do to increase their data security? They download the latest antivirus software, implement a data encryption protocol and/or install a firewall. Unfortunately, all these will not do much good if malware is introduced into the system from inside, i.e. by an employee.
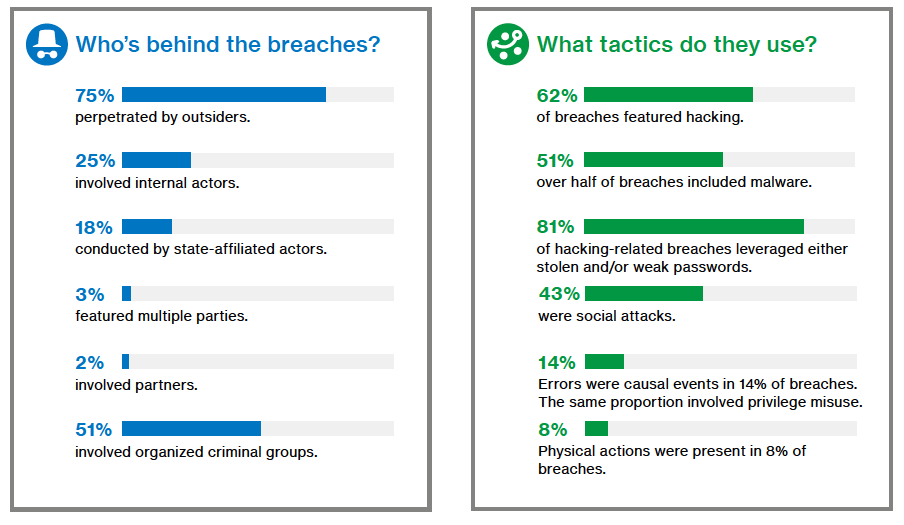
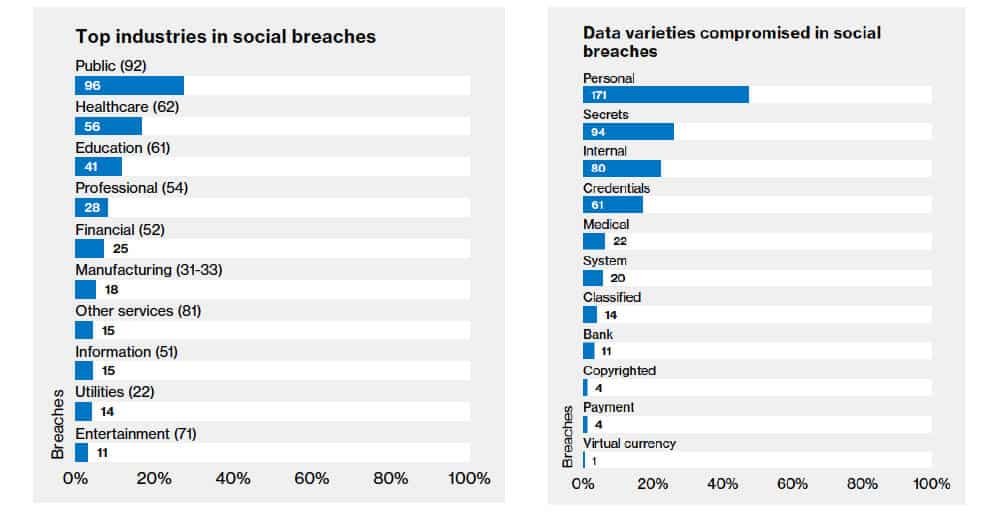
This might not be enough…because social engineering is responsible for 43% of all recorded data breaches, according to Verizon’s Data Breach Investigative Report for 2017
The graphic below, taken from the above mentioned Verizon’s report illustrates this quite nicely:
What Is Social Engineering?
Social engineering is a method of using psychology to gain access to the computer systems and tricking the victims into giving out sensitive and personal information such as passwords and other credentials. How often have you held a door for another person and let them into an apartment building or even the workplace? Or received an innocent looking email from a friend with an attachment or a link?
Let’s take a look at the most common social engineering techniques.
1. Phishing
Phishing is the most common social engineering technique used by cybercriminals today. Phishing uses a fake email from a third party the victim would trust to trick them into providing sensitive information. The victim could be receiving an email from what appears to be their bank or Paypal for example, asking them to log in to the website. The reasons are varied. You could be told that your account was compromised (oh the irony) and you need to update your password; or that the bank is updating its privacy policy and you need to log in to confirm that you agree. Once the login is complete, the hacker receives the credentials. BAM, you’ve been socially engineered!
Another way phishing works is sending a fake message from a “friend”, a “coworker” or another person you might trust. This message will ask you to open an attachment (how can we resist checking out a football infographic or a news story about that scandalous celebrity). A hacker might utilize email, text message or social network messaging to pull off this scam. Once you opened the attachment or clicked on the link, a malware finds its way into your computer system. BAM! Your computer data is now at the mercy of the hacker.
Even though we all know to triple check the source of any email, the reflex to click on a link or follow instructions to log in is almost automatic.
It’s so effective, simply because it works.
2. Vishing
Vishing employs the same idea as phishing, just over the phone. Think about the last SPAM call you got, talking about a cruise you have “won” and the information you need to provide to receive your prize. This is a prime example of vishing. The scammers will ask you for your personal information such as date of birth, address, financial information, etc. Or you could receive an email from your “bank” asking you to call the bank’s number to confirm your identity. Of course, you’d be calling the scammer instead.
Cyber Risk Management Guide
One example is a scam that has been used since at least 2009. A hacker, posing as Microsoft solutions architect, will call an organization’s employee and inform them that their computer has been infected with a virus. Then typically the employee is directed to download software from “Microsoft’s” website to fix the situation. The unsuspecting employee doesn’t know that she is really downloading a malware.
3. Pretexting
Pretexting is yet another technique that is similar to phishing. Where phishing preys on the victim’s fear or urgency to do something, pretexting capitalizes on human’s desire to trust. The hacker builds a false sense of security and trust with their victim.
Pretexting scam requires a lot of research on the part of a scammer, concocting a story that leaves little doubt that it’s safe to give them the information requested. Some scammers also use pretexting to gain access to the organization’s physical location by pretending to be an employee of another branch, an auditor, etc.
For example, upon researching a large company with multiple locations, a scammer is likely to exploit the fact that employees from different locations don’t interface with other location often. Imagine, another “employee” coming to visit your branch, saying they are CFO’s assistant. They have the right story, say all the right words, know all the right facts about the CFO and the company. You have no reason to not believe them.
After all, it’s entirely possible that they are a new hire that you somehow missed an email. They might even have a badge (fake of course)! So you might not think twice about providing them the financial reports they “need” for their branch. What just happened here? The scammer has your company’s sensitive financial data and to make it worse you have been conned to willingly provide it to them. That’s pretexting.
4. Baiting
Everyone likes to get free stuff, right? A free download of a popular song, a movie or an app. What could go wrong?
If the scammers are behind this, then most likely your computer has been compromised as soon as you began that download. Baiting promises a free good, like a song, in exchange for your information. Once you provide the sensitive data the hackers are after, the virus is downloaded onto your computer.
Illegal torrents that go around copyright laws are notorious for containing malware and viruses and are a good example of baiting.
5. Quid Pro Quo
Quid Pro Quo involves a promise of service (unlike in Baiting which promises a good like a movie or an app) in exchange for sensitive information. The most common Quid Pro Quo scheme is s scammer pretending he is an IT consultant or a customer support representative calling the employee back. Eventually, he’ll hit on the employee that really does have a problem. The “fix” will usually involve revealing sensitive data like a password and other credentials.
Other less sophisticated Quid Pro Quo schemes might involve a workplace contest or a survey.
6. Tailgaiting
This social engineering technique doesn’t use the email or another online medium to gain information. Instead, the hacker gets close and personal with his victim. Tailgating is used to gain access to a secure building by blending in and making you think that the hacker truly belongs there. At the beginning of the article, we gave an example of letting someone you don’t know into an apartment building or a workplace.
This is a prime example of tailgating. Imagine a professional looking woman, with her hands full with purse and coffee and maybe another bag struggling to pull out her badge (or you are assuming that she is trying to pull out or find her badge). If she asked you to help and open the door, wouldn’t you graciously help? Of course, you would.
Some confidence on the part of the hacker, a good story, small talk and a bit of acting abilities and you are bound to never even suspect that you just allowed a hacker into the building.
The Verizon data breach report we mentioned earlier further illustrates the impact social engineering across industries:
An Example of Social Engineering: Baiting
A good example of baiting is an experiment that Steve Stasiukonis, VP and founder of Secure Network Technologies conducted back in 2006 when he was hired by a credit union to assess their vulnerabilities.
His team implanted a Trojan virus on flash drives that were left unattended in the parking lot, outside lunch spot and other areas employees frequented. Within a day the data started trickling in. The Trojan was designed to collect passwords once the flash drive was plugged in. Out of 20 drives, 15 were found and fired up by the unsuspecting, curious employees.
If it was a real hacker, all they would need to do is sit back and collect passwords with little chance of being caught. A pretty scary experiment, don’t you think?
Insurance That Covers This Risk
With the cybercrime on the rise, insurance companies have developed a stand-alone comprehensive insurance product to mitigate the financial and reputational loss after the cyber attack. With the ability to cover a loss of income due to the attack, the mandatory notification requirements, credit monitoring to affected parties and the cost of forensic investigation, Cyber Insurance and Crime Insurance are products that every business should seriously consider.
The loss due to social engineering attack can be covered as well.
According to Ponemon Institute, data breach incident on average costs a business $141 per potentially compromised record. The total cost could be in hundreds of thousands of dollars, depending on the type of data you store and how many records were potentially accessed.
As you can see Cyber Crime is a real danger to your business. While antivirus software and firewalls help detect viruses trying to access your systems from the outside, no firewall can protect your organization from human nature and introducing the viruses from within.
Empower your business with a proactive approach to cybersecurity through a comprehensive security awareness program. This program equips your employees to identify and mitigate social engineering threats, safeguarding sensitive data and minimizing risk management challenges.
However, proper insurance coverage is an important backstop for when your best efforts come up short and data is compromised. A well-crafted insurance policy can protect you when a social engineering hackers strike and you have nowhere else to turn.